Work does not always require an employee’s presence in the office. In many cases it is acceptable, convenient, and sometimes advantageous for the employee to work remotely from a mobile device. Receiving and sending email, working with documents and corporate network resources are all possible on a smartphone or a tablet.
The use of mobile devices within the corporate network present a number of serious and painstaking tasks for the IT department like connectivity and configuration, security issues, software updates and device usage control; when the number of mobile workers in the company exceeds a certain amount, manual operation becomes impossible. But it is not necessary either for there are many MDM systems (Mobile Device Management), which automate most of these tasks. In addition to assisting the IT department’s efforts an MDM system can provide a higher level of convenience and security, which is hardly attainable without it.
One of the most functional MDM systems on the market is included in Kaspersky Security for Business. Being integrated in Kaspersky Security Center the system is capable of providing the full range of opportunities for corporate clients while maintaining the high level of information security.
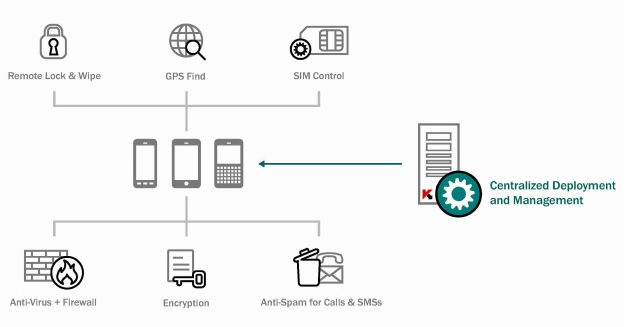
Operational diagram of Kaspersky Security for Business with the management of mobile devices
The development of Kaspersky Security for Business is based on the following priorities:
- Mobile device protection from the full range of cyber threats without involving third-party products (antivirus programs, firewalls, etc.).
- Integration with enterprise security systems. The company should be able to apply, for example, the same content filtering to workstations and mobile devices.
- Simple and user-friendly systems. To connect to and use the system a user does not have to use any skills that go beyond the basics of handling devices. All setup and installation steps must be performed remotely by the administrator.
- Wide coverage of client devices vary within the BYOD principle with supporting almost all mobile operating systems and hardware platforms on the market.
- Management of all system’s functions from a single console with respect to both stationary workplaces and mobile devices. The convenient and effortless administration is the surest way to provide reliable operation of the system.
- Low total cost of ownership. The product must provide the maximum range of the required functions for mobile device management and assured security without involving third-party products.
According to these principles a mobile device connected to the MDM system of Kaspersky Security for Business should be a valid part of the corporate network without reducing the overall level of information security.
Connection and installation of software
What does it look like to a user? Due to the above principle, it looks easy. To get started with an MDM system the agent must be installed on the user’s device. There are several ways to install:
- Following a common hyperlink posted on the corporate site or printed on paper in the form of a QR code. The employee just needs to click on the link from the device and the agent is installed automatically, the user does not have to enter any additional data.
- Following a private link sent via SMS or email to the employee’s device. Similarly installing the agent does not require any specific skills or actions.
The installed agent synchronizes with the MDM server and applies default profiles and security settings or, in the second case, the custom ones for the user. The next step is to install the basic set of enterprise software – the agent performs it all by itself.
If the administrator gets an application, which is required by the user and trusted, you need to create an installation package. In the installation packages control panel you simply click the tab “New”, enter the name of the package and specify the path to the executable file of the application.
After creation the installation package is posted on the web server. The user can download it following the link generated while creating the package.
If the user needs to run additional applications for work he may come to the corporate applications site with approved applications for employees’ mobile devices and install all the necessary software in just one click.
Upon completion of the installation, the software and hardware platform audit will run. The administrator can configure multiple types of reactions to certain instances, for example, to detect a jailbroken iPhone or a rooted Android device. In some cases the administrator is just notified, in other cases the device can be automatically blocked as threatening to break the information security. The administrator can also control some security-related hardware parameters (for example, he can disable certain interfaces).
Security of data and applications
The foundation of protecting the client device within Kaspersky Security for Business is Kaspersky Endpoint Security for Mobile Devices. This application implements the multilevel data protection. Here are the main security features of the product:
- Containerization of data and applications. The administrator defines which data and applications received by the device from the corporate network are to be enclosed in a container. All containerized data are encrypted to prevent information leaks even with malware present in the system. Moreover, the container allows control of the application’s access to the hardware resources of the device, including sending SMS, camera operation, navigation tools and file system.
- Checking the downloaded files, including archived ones.
- Hiding the display of confidential contacts, both containerized and non-containerized.
- Protection against network attacks.
- GPS location of the stolen device and deleting data on it.
- SIM card change detection with various responses to it (locking the device, sending messages to the owner and administrator, etc.).
- Remote administration of security options.
Centralized security management on the mobile device with the help of Kaspersky Security for Business
Besides that, Kaspersky Endpoint Security for Mobile Devices can comply with third party MDM systems, such as Sybase Afaria and Microsoft System Center Mobile Device Manager, providing comprehensive data protection without any conflicts with the control agent.
Casual work
After installing the agent and the necessary software, the MDM system operates quite transparently for the user, almost without impacting the device (according to the data obtained after testing, the device’s energy consumption increases by less than 5%).
Each client device can have the synchronization cycle of its own due to the user’s needs and the intensity of use (for example, while roaming the frequency synchronization is reduced to a minimum). During every synchronization, the system updates the security profiles and lists of filtered content, installs patches and updates the applications.
If necessary (for example, at the request of the user or in accordance with the requirements of the security policy) the administrator may configure the device within certain limits from the console like setting certain hardware options, uninstalling and installing applications and uploading all sorts of data on the device.
Let us consider some typical working scenarios. All functions related to configuration and security of mobile devices are assembled in a single menu.
After selecting the needed item, the administrator can perform all necessary actions in just one click when it is needed.
– Installing or uninstalling the program. If the administrator has created an installation package, install it on your device clicking the option “Install application to device”. Similarly when removing select “Uninstall application from device”.
– Loss of the device. Without any important information on the device it can be remotely locked (select “Lock device”). The finder of the device will not be able to use it but see the message on the screen specified by the administrator (e.g, an address where to return the device to).
– If the device contains important data, and there is a risk of its leak, all data on the device can be purged by selecting “Purge device”.
– A trip abroad with the device. Using a smartphone or a tablet while roaming may be expensive. If the employee is abroad with the device without bothering to configure it the administrator can remotely set the parameters of work on roaming by selecting “Set options for roaming devices”.
The functions of security and device management are implemented to ensure their execution with minimal effort from the administrator – “just one click”. The underlying principle is also the concentration of management functions in a single console. This ensures the relative ease of mastering the console’s interface and the simplicity of the MDM system administration. By these criteria Kaspersky Security for Business is one of the top solutions on the market for such systems.
 Business News
Business News