A modern man cannot imagine his life without mobile devices like smartphones and tablet computers. A portable minicomputer that provides access to the Internet and offers basic features for processing documents is often sufficient. It keeps you online wherever in the world you might be and can be very convenient, and that is why people tend to use their own mobile devices for work if their company lets them.
This may make the lives of employees easier, but it generates plenty of problems for the IT-department. Each device must be configured to provide access to email and corporate contacts, have instant messengers installed, and even be connected to the corporate network via VPN. And that is not even the biggest problem, for after an employee’s personal smartphone has been connected to the corporate network, it becomes not just a work tool, but also a gaping security breach given the uncontrolled usage of an employee for his or her personal needs.
If there are more than 10-15 employees it would require specialized administration tools, which abound on the market in the form of Mobile Device Management (MDM) systems.
Pocket source of threats
For a long time, the BlackBerry Enterprise Server (BES) was the only remarkable MDM system on the market. The product is powerful, but it has a great flaw to it: it works with BlackBerry mobile devices only. Because BlackBerry smartphones are handy in conjunction with BES only, few people use them in everyday life, preferring iPhones or Android devices instead. When applying for a job in a company that uses BlackBerry, an employee surely gets the appropriate smartphone. As a result, he or she is forced to carry two devices – a personal one and an office BlackBerry. So there are two phones, each with its own list of contacts, each to be periodically recharged. A set of rules needs to be considered in this scenario: which device is for calling whom, what email account is set up on either device, who pays for the costs? This is obviously awkward, and people do not like it, therefor users feel much more at ease when their own devices are hooked up to the corporate network.
To meet the customers’ needs the concept of BYOD (“Bring Your Own Device”) was born. It appears simple and elegant: when applying for a job an employee brings his or her favorite smartphone, the IT-department connects it to the MDM system, and the employee gets the entire range of approaches and opportunities for mobile work.
However, this approach dramatically complicates the task of MDM system developers. It’s not just individual components that have to be developed for the four most common mobile operating systems (iOS, Android, Windows Phone, Symbian), even hardware platforms differ a lot. Even if you ignore all the smartphones and tablets that are over three years old, it would turn out that the system needs to be tested on dozens of devices. And there is a persistent risk that the MDM agent would fail to start on the employee’s favorite smartphone on, say, a business trip to Malaysia.
In other words, BYOD is a serious challenge to developers. This is the reason why most MDM systems have not gotten 100 percent support of modern mobile devices, i.e. they do not fully agree with the BYOD concept.
According to a survey of 3,300 IT professionals in 22 countries by B2B International in the spring of 2013, almost half of the companies let their employees use the resources of the corporate network via their own devices with just a small part of the companies having found the right MDM system.
Security and threats
Assured security is another major problem with connecting employees’ personal mobile devices to the corporate work.
Cybercrime threats hold one of the top positions in the list of business IT risks. According to the survey of B2B International, the most important threats to businesses are comprised of industrial espionage, intellectual property theft and fraud. These crimes existed long before mobile devices and information technologies appeared, but recently cyberattacks have become the most effective tools for criminals.
Over 50% of respondents added cyberattacks to the list of critical business risks. By this criterion, cyberattacks crushed other factors like political instability, high crime rate, natural disasters and terrorism, being second to unstable economics (55%).
The sharp increase of cyberattacks has not gone unnoticed either, as 52% of respondents noted an increase in the activity of cybercriminals. In the twelve months before the survey, 91% of organizations had been cyberattacked at least once. The most frequent type of threat was malware, afflicting 61% of the surveyed companies. Another 14% lost important business information from attacks, and 20% of those attacks were the consequence of stolen mobile devices. Out of those that had devices stolen, 5% of cases suffered from a loss of important information.
The smartphone is traditionally the least protected device against cyberattacks. The majority of office workers are sensitive to measures of information security. Restricted access to web resources, the inability to install applications on their own and the requirements of rigorous password changes are all necessary evils to employees. But when it comes to a personally purchased smartphone, the attitude is quite different.
“It is in my pocket, what will happen to it?” is the standard user attitude of someone who has access to corporate emails and documents on his or her phone, on the same device he or she uses to surf the Web just for fun, enjoy a variety of web services, and click on links received from friends. If the phone is not protected, it is vulnerable to cyberattacks. In some cases, the user does not have to do anything: attackers can do without any help when planting malware on a smartphone, and then they can easily read emails, download important documents and sometimes get access to other resources on the corporate network, such as file servers.
As the statistics of detected malware for mobile devices show, hackers have been using this option at an accelerated pace. In 2012, there was an explosive growth in the number of malicious programs.
In 2013, the volume of mobile malware continues to grow. On June 1, 2013 the total number of malware modifications and families in the collection of “Kaspersky Lab” exceeded 100,000.
The malware distribution between platforms
The diagram clearly shows the imbalance of malware distribution between platforms: the bulk of threats befell Android due to the openness and prevalence of the platform.
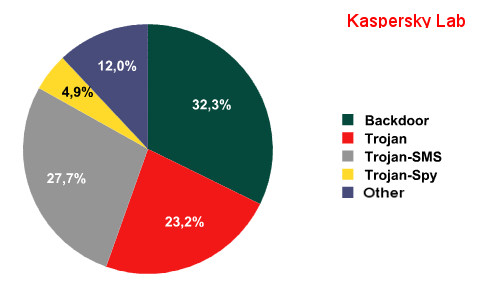
The distribution of malware types:
Note that, until recently, the most popular type of malware was an SMS-Trojan that sends short messages to premium-rate short phone numbers owned by hackers. Now programs of a wider application have come to the fore: all kinds of backdoors, spyware and multifunctional Trojans.
The Android Trojan Backdoor.AndroidOS.Obad.a is an example of a mobile Trojan of the latest generation. This malware exploits an Android OS vulnerability to obtain the DeviceAdministrator rights without being displayed in the list of applications with such rights. It also tries to get superuser (root) rights and contacts its owners via any available means, whether it is an active Internet connection or a wireless network that does not require authorization. After that, the malware’s command server takes control over the device with an option of sending commands via both the Internet and SMS.
In addition to the standard mobile Trojans tools of enrichment like sending SMS to premium-rate numbers, Backdoor.AndroidOS.Obad.a has many other functions. It can act as a proxy to install applications received from the command server, send back the information about applications and the user’s contacts, and transfer files to all detected Bluetooth devices. As to the complexity and the number of exploited unpublished OS vulnerabilities (three!), Backdoor.AndroidOS.Obad.a is very close to malware for Windows.
The active usage of mobile malware for targeted attacks on companies is just a matter of time. Mobile malware already has virtually all of the required functionality.
One striking example of this kind of a tool for targeted attacks is the mobile version of FinSpy, the application British company Gamma International developed for government organizations.
FinSpy is a tool for remote monitoring, capable of recording incoming and outgoing calls, wiretapping through the device’s microphone, retrieving call logs, SMS/MMS, contacts and so on, as well as tracking the user with the help of GPS. Gamma International develops versions of its software for virtually all mobile platforms: FinSpy may be found on a BlackBerry and on Windows Mobile or iOS devices. Besides the “official” FinSpy, there is a lot of not so well-known spyware (FlexiSpy, MobileSpy, etc.) with a similar range of features and all aimed at companies in the private sector.
Such threats highlight mobile security. Protecting a phone is more difficult than securing the corporate network, many MDM systems recoil at this stage, passing some safety issues to third-party software, which brings additional expenses on implementation and support, therefore, increasing the cost of ownership. Thus, there is a paradoxical situation on the market: on the one hand, mobile threats are becoming increasingly important; on the other hand, many popular MDM systems ignore this aspect of security.
In the next part we will focus on the technical aspects of MDM systems and their quality criteria. To be continued.
 BYOD
BYOD

 Tips
Tips