The old vulnerability that had been exploited by the notorious “battle-worm” Stuxnet, is still around, affecting millions, even though a patch for it had been released years ago.
The vulnerability in question is CVE 2010-2658, discovered in 2010 and present in Windows XP (which means that it was probably there for up to nine years prior), as well as Vista, Windows 7, and Windows Server 2003/2008.
It was patched (relatively) promptly by Microsoft: Stuxnet had been discovered in June 2010, Microsoft acknowledged the problem on July 16th, 2010, which was followed by the patch on August 2nd, the same year. According to Microsoft, this vulnerability allowed “remote code execution if the icon of a specially crafted shortcut is displayed. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.” The problem was designated as critical.
4 years passed, Stuxnet’s vuln is still around #enterprisesec #protectmybiz
Tweet
Four years have passed since then. Between November 2013 and June 2014 Kaspersky Lab conducted a research titled “Windows usage and vulnerabilities“. According to its findings, Kaspersky Lab’s detection systems still register millions of instances in which malware exploiting vulnerability CVE-2010-2568 is detected. Within the research period over 19,000,000 users encountered this threat.
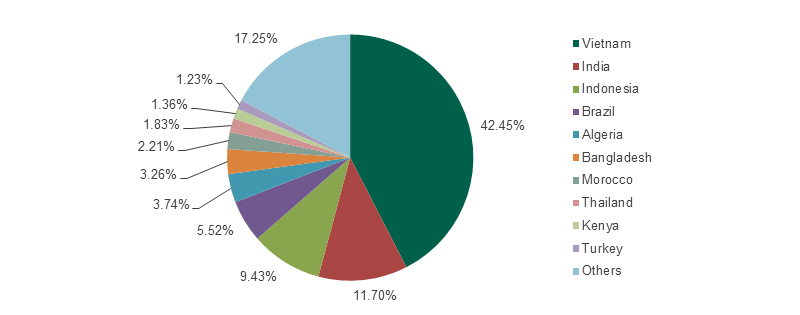
The malware instances targeting this vulnerability were most often detected on the computers of users residing in Vietnam (42.45%), India (11.7%), Indonesia (9.43%), Brazil (5.52%) and Algeria (3.74%). See the graphics below:
It’s not a surprise that Vietnam, India, and Algeria are on the list of countries with most CVE-2010-2568 detections, and among the leaders in terms of the numbers of users still using Windows XP, which support had been dropped by Microsoft in April this year.
That very operating system occupies first place for CVE-2010-2568 detections: 64.19% of detections were reported from computers running under Windows XP. Again, no surprise here.
Windows 7, currently the most widely used in the world, is only in second with 27.99% detections. Next comes Windows Server 2008 and 2003 with 3.99% and 1.58% detections respectively.
In this specific case, the large number of detections does not directly translate into a large number of attacks. ACtually, due to the peculiar ways this vulnerability is exploited, it is impossible to accurately differentiate between cases when Kaspersky Lab’s product protected from real attacks involving malware exploiting CVE-2010-2568, and the cases when they only detected vulnerable shortcuts automatically generated by a specific worm.
But still the large number of CVE-2010-2568 detections is a testimony to the fact that globally there are still many computers that are vulnerable to attacks involving malware exploiting this vulnerability. This is also a distinct sign that these PCs are also subjects to many other vulnerabilities, at least part of which are exploited by malware. Poorly maintained Windows XP machines with security solutions are the main “fodder” for botnets today, which means that they are also a source of global IT security problems. A source that is yet to stay for some time.
Windows XP is the main “spawning grounds” for malware. #security #windowsxp
Tweet
Regarding the aforementioned vulnerability and detections, Kaspersky Lab’s experts presume that most of these stem from poorly maintained servers without regular updates or a security solution installed. These servers may also be inhabited by worms that use malware exploiting this vulnerability.
Following their designed logic, such malware programs routinely create malicious shortcuts in a general access folder; and each time a user protected by a Kaspersky Lab’s solution gets access to that folder and clicks on such a shortcut, the detection takes place. This is an obvious risk of malware infection in the organizations using these servers – and PCs.
Once again there is a reason to call for a global IT Cleansing campaign among the users and businesses. IT security is everybody’s business and in the interconnected world negligence of one server may pose big problems for many people at once.
Additional details on this research are available at Securelist.
 PC neglect
PC neglect

 Tips
Tips