Corporate IT Security Risks
Special Report Series 2016
Introduction
In 2015 and early 2016, Kaspersky Lab registered a large number of cyber incidents involving ransomware, many of which have drawn a wide public response. Compared to the period of 2014-2015, the number of ransomware-based attacks on the corporate sector increased sixfold. Kaspersky Lab experts expect that in frequency of use, this type of malware could even surpass banking Trojans.
In order to find out more about the challenges and threats businesses are encountering, Kaspersky Lab, together with B2B International, has conducted a study entitled Corporate IT Security Risks Survey 2016. We asked more than 3,000 representatives of small and medium-sized companies how they manage to cope with cryptomalware in the constantly changing landscape of cyber threats.
Here’s what we have found.
42% of VSB and 49% of SMB representatives say they consider cryptomalware to be one of the most serious threats that their organization could face. This type of ransomware has entered the Top three digital threats which cause serious concern for companies worldwide.
This perception meets the worrying reality. Survey findings reveal that 20 % of companies worldwide have been subjected to IT security incidents as a result of a cryptomalware-based attack. For smaller companies, ransomware ranks second in the list of threats, most often resulting in the loss of large amounts of data.
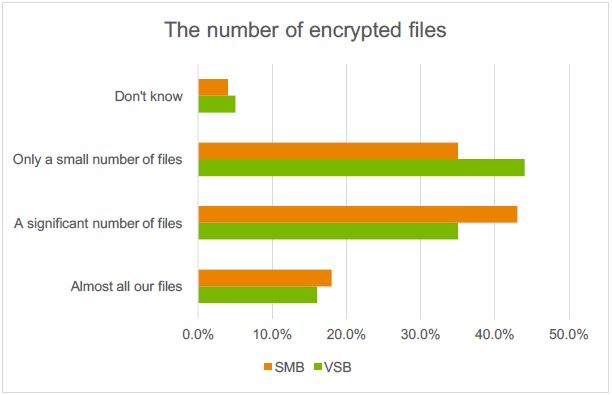
What are the reasons behind efficiency of cryptomalware-based attacks? Once a malicious program penetrates the system, the user has almost no chance to get rid of it without losing valuable data. On average, attackers demand $300 for the decryption of files. However, the consequences caused by cryptomalware infection are not limited to one-off payments and include losses caused by business continuity disruption. According to the Corporate IT Security Risks Survey 2016, the average amount of damage caused by one cryptomalware attack may cost small and medium businesses up to $99,000.
The cost of cryptomalware
The total amount of damage caused by cryptomalware can be divided into two parts: the ransom and the related losses.
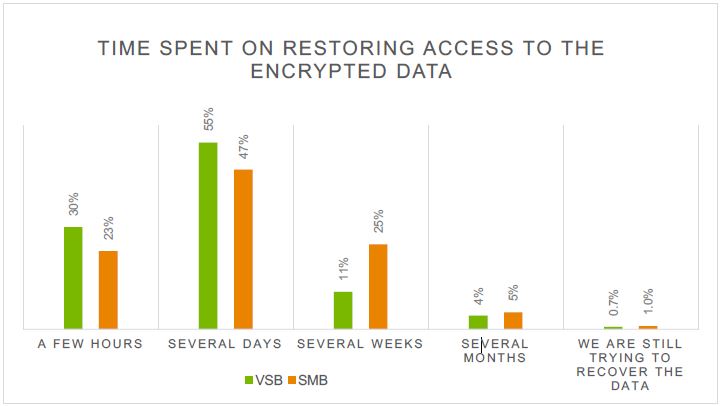
For smaller companies, even a short-term lack of access to corporate data could cause significant losses or completely suspend their activity. If the organization has not taken appropriate measures to ensure the safety of its critical information, purchasing a decryption key may be the only way to resume its operations. Despite the fact that cybercriminals do not guarantee the return of corporate data, 34% of entrepreneurs admitted paying extortionists. The IT Security Risks Survey 2016 research shows that one out of five companies has failed to get back its data after paying a ransom.
The amount of related damage is, to a large extent, affected by shortcomings in the preventive work of the IT staff (poorly administered systems, outdated or missing backups, unreliable passwords, irregularly updated software, etc.). According to the IT Security Risks Survey 2016 research, about 67% of SMB representatives have reported complete or partial loss of corporate data due to cryptomalware.
For many small and medium businesses, the lack of resources and internal expertise in the field of information security is one of the most serious problems. According to the survey, over 44% of entrepreneurs admitted their knowledge about IT threats left much to be desired. About 43% of respondents stated they needed more effective protection, while more than half of the organizations surveyed reported the need for experts not only in IT but in information security.
How to reduce the risk of data loss?
Cryptomalware is distributed via two main ways:
- Drive-by downloads when visiting compromised web sites. An exploit kit is a malicious software designed by cyber criminals to identify software vulnerabilities in user PC communicating with it, and discovering and exploiting vulnerabilities to upload and execute malicious code on the client endpoint. For example, CryptXXX used Angler kit to exploit vulnerable browser-related applications and deliver Bedep, a downloader that grabs CryptXXX and click-fraud malware.
- E-mails with malicious attaches and links which imitate ordinary communication: a tax notice, acts and contracts, information about purchases, etc. By downloading and opening the attached file, the user unwittingly runs malicious code. Cybercriminals used this tactic with Scatter (Trojan-Ransom.BAT.Scatter/Trojan-Ransom.Win32.Scatter), when an employee received an email allegedly sent by the representative of a partner company. The message mentioned that some documents, related to the companies’ joint operations, had been lost, and a copy of them was requested. The attached file supposedly contained a list of these documents. In fact, it contained the Trojan, which was then launched by the user and resulted in IT incident.
SMBs can adopt several tactics to deal with the threat of fast-paced cryptomalware.
- First and foremost, the threat should be addressed with basic IT Security staff training. According to the research, one in five cases related to significant data loss occured due to the carelessness or unawareness of employees. Staff should be educated so that they exercise caution when opening suspicious emails and unknown links, especially as cybercriminals often distribute cryptomalware via fake e-mail messages mimicking notifications from an online store or a bank, or imitate ordinary communications. Enabling antispam settings also helps to avoid IT incidents.
- Put a process in place to create and safely store backups. If an IT incident occurs, the restore point could save almost all important files, including accounting documents, client data, legal documents etc. The regular backing up of critical records is therefore essential.
- Control access to corporate data. Most companies use shared folders to create a central space for employees to collaborate on files. Restricting access helps to prevent the spread of cryptomalware. If the workstation is infected, ransomware can cause less harm to the system partition or the operating system, due to a lack of administrator rights.
- Update software on all devices to the latest version. Cybercriminals try to exploit vulnerabilities in software to compromise systems. This relates to the operating system, browser, and other widespread office programs. Regularly updating the patches could help the company to avoid these IT threats.
- Use professional software to protect what matters most for your business. To ensure business-critical data and infrastructure protection, companies can take advantage of a holistic portfolio of Kaspersky Labs business products. These solutions leverage cutting-edge technologies, enabling multi-layered protection from known and existing threats, including cryptomalware.
In most cases, security solutions block ransomware with no extra help. Nevertheless, to deploy and configure the security products, companies need IT specialists with a solid knowledge and skills. The IT security department is the last line of defense in protecting the corporate network.
Smaller businesses that cannot afford in-house IT specialists can leverage external security expertise, delegating control of IT systems to managed services providers (MSPs). The contractor company specialists will install the appropriate software and will help to evaluate the protection levels of business-critical data and processes.
 Infosec
Infosec
